Two Factor Authentication
... everywhere
Cornelius Kölbel, Ohio Linux Fest, Nov 2nd 2019https://privacyidea.org/talks/OhioLinuxfest-2019/2FA-everywhere.html
Agenda
- About me
So you know, what you can ask me. - Demystifying 2FA
... or rather mystifying it? - privacyIDEA
one system to rule them all! - Integration with any application
2FA is a matter of communication!
About me
...since 2005
2005
- Reseller: eToken (NG OTP), Smartcards, PKI, HSMs
- Strong authentication, Encryption, Full HDD Enc
- PKI
2006
- Vendors: FreeRADIUS-Plugin (LinOTP) for eToken NG OTP
2009, 04/2010
- Vendor / Product Management:Enterprise ready Open-Core Software (LinOTP2) for eToken NG OTP and others (Note: No Google Authenticator at that time!)
09/2010
- Google misuses the HOTP algorithm for its Authenticator
2010 - 2013
- Vendor Deploy more mechanisms
- Smartphone with Authenticator :-/
- SMS OTP! :-/
- OCRA (does not lift up)
- TiQR
- U2F? Ah - no!
2014
- "Vendor"
- Own Open Source strategy → Fork to privacyIDEA
- Rewrite for more modern technologies like Flask, AngularJS, Bootstrap
- Founded company to provides services and support
since then: privacyIDEA
- The factor is free to choose
- Important aspects are:
- Integration in to your processes
- User acceptance
- Sustainability (Don't go EOL)
- Costs - not only "licenses" but also internal costs.
Successful 2FA is a matter of smooth workflows.
Two Factor Authentication
- How are you doing 2FA?
- ... as an end user, admin, in your company...?
What people thing, what 2FA is ...
- Two Factor
- Two Way
Two Factor - can be the same way
Something you..
- ... know,
- ... have,
- ... are.
What in fact is two factor authentication:

What is no 2FA...?
Two Passwords (Password and "PIN")
Two Apps on one Smartphone (boils down to one "possession")
Classical possession
Smartcard, Credit Card, OTP-Token, SSH-Key- Can not be "guessed"
- Can not be brute forced
- Need to "steel" it
- cryptographic key material (symmetric, asymmetric)
- Quality level: protect the key material (no copy)!
Quiz about 2FA...
What is no "possession"?
(Mind the cryptographic component)SMS / text message
What uses an HMAC based message authentication code (HMAC)?
HOTP, TOTP (RFC 4226, 6238) - with a symmetric key
What uses asymmetric crypto like RSA or ECC?
Smartcards, U2F, FIDO2
What uses strong, non broken HASH algorithms?
Passwords
What uses proprietary algorithms?
Biometrics
2FA is more than one 2nd factor
Organizational challenges
Enrollment problems
 read the blog post.
read the blog post.
Problem: Users are not tech-savvy
Problem: My device is not supported!
Problem: Which vendor should I trust?
Problem: Backup - not only your single device, but all tokens of your company!
Problem: (Helpdesk) processes
2FA is more. It means...
- Infrastructure
- Management
- Workflows
2FA needs a
2FA Management and Authentication System
- This is why proprietary vendors sold licenses for cra*** software.
- This is why they now bill high fees for cloud services.
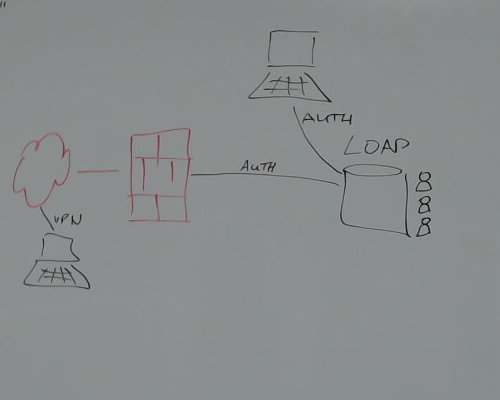
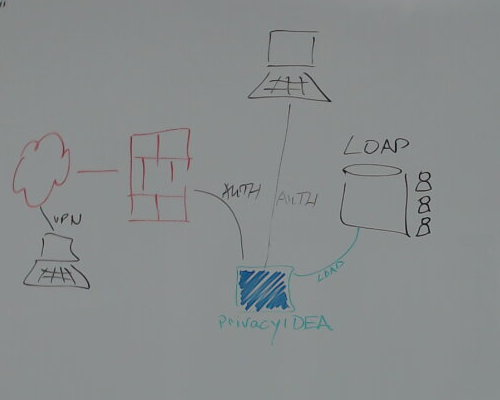
Your application
Should do no 2FA itself! (Word*****, Next*****, Free***, Key*****)privacyIDEA Authentication System
privacyIDEA is not...
- an identity management system,
- a VPN,
- a firewall,
- ...
...but a token management system
and authentication server for two factor authentication.
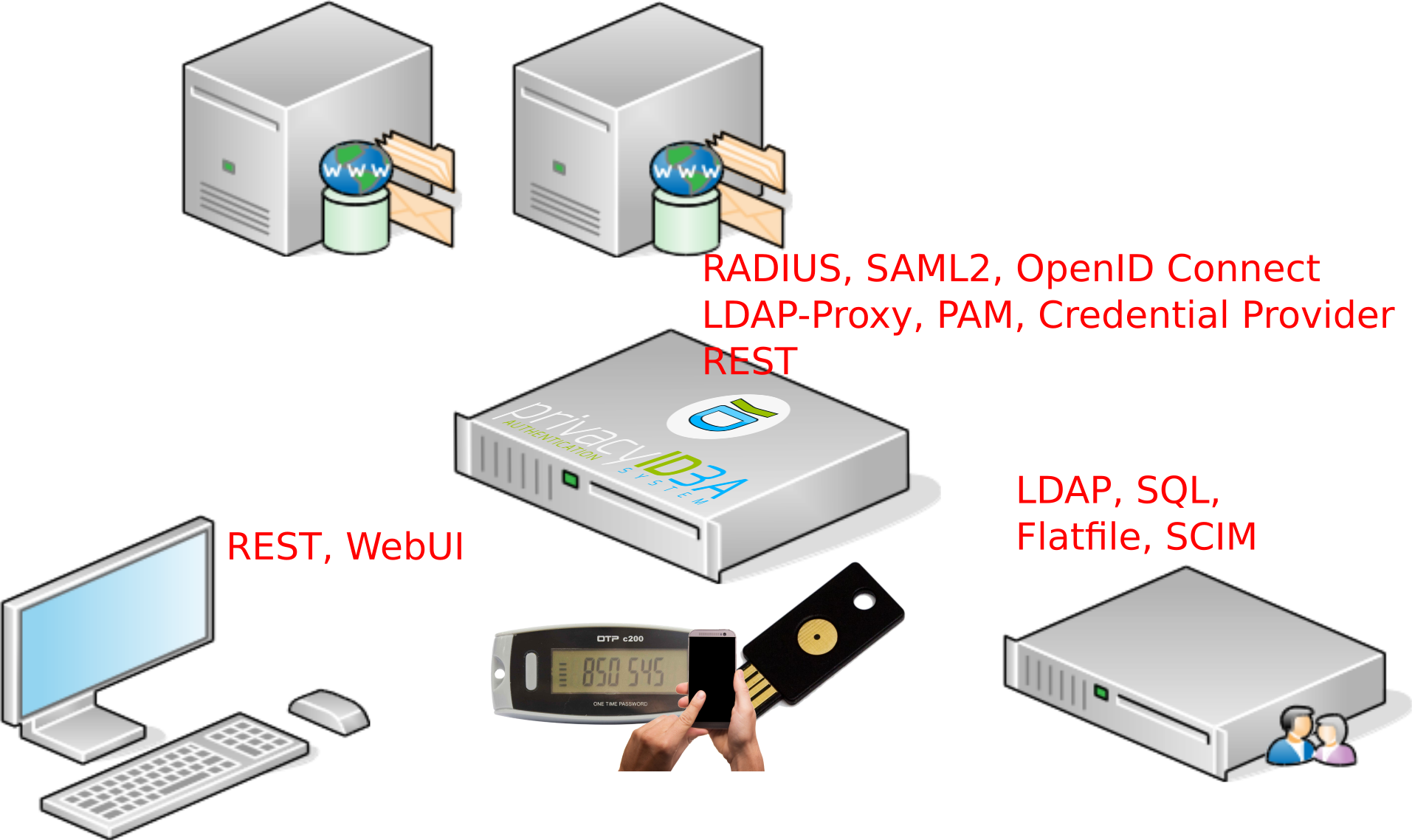
Software Stack
- REST-API
- Python Application (Flask) (2.7 - 3.7)
- Apache2 or NGinX
- SQL database (SQLAlchemy): MySQL/MariaDB, PostgreSQL, Oracle...
User
Read access (write possible) on
- LDAP
- SQL
- Flatfile
- SCIM
...mix and match as needed (read
realm concept).
token types
hardware, software and virtual tokens:- Hardware: Key fob, OTP cards, Yubikey, Nitrokey, U2F
- Software: Smartphone apps, PUSH token, x509 certificate, SSH key, paper/ TAN, questionaire, register, password...
- Virtual: Forward/remote, RADIUS, 4-eyes
policies
determine the behaviour of the system. Possible Scopes:
- Admin / User
- Authentication
- Authorization
- Enrollment
- WebUI
- Register
Policies depend on:
- users
- arbitrary user attributes
- arbitrary HTTP headers
- administrators
- time
- client IP
event handlers
can trigger additional actions. Event handler modules:- Notification
- Token
- Script
- Counter
- Federation
- Request Mangler
- Response Mangler
- Notification File Writer
This way you get better (automated) and more flexible workflows.
recurring tasks
- count events
- create statistics
Integrate 2FA with your application!
Everything is fine...
if your application already provides standard protocols- PAM → pam_radius, pam_python/privacyidea
- RADIUS → FreeRADIUS
- SAML2 → simpleSAMLphp, Keycloak, ADFS
- OpenID Connect → Keycloak
What we want to do alternatively
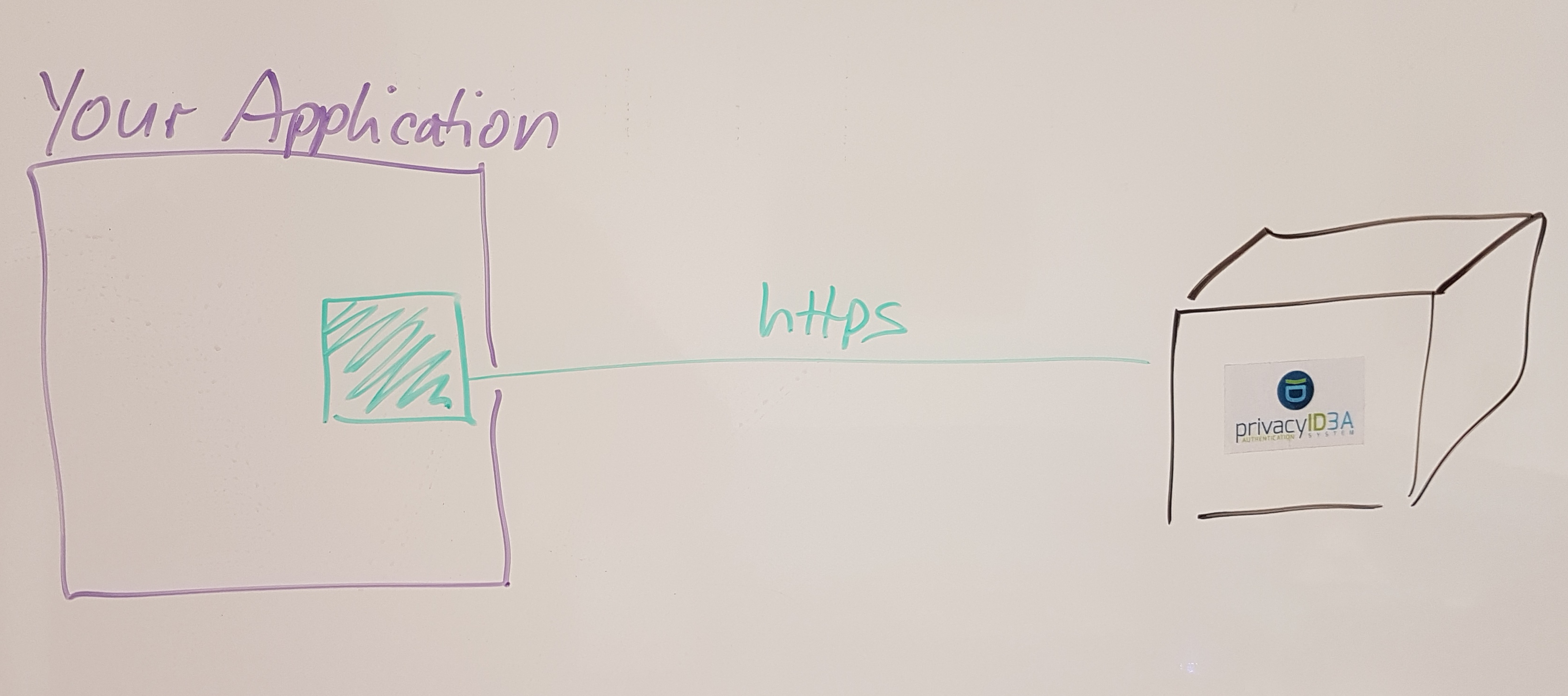
Integrated e.g. with:
- Wordpess
- TYPO 3
- Django
- Keycloak
- simpleSAMLphp
- ownCloud
- FreeRADIUS
- benno mail archive
- ...
The green plugin in your application:
- decent authentication stack
- ability to write plugins
credetials need to be sent to privacyIDEA, how?
The privacyIDEA REST API
There is nothing but the API.
https://privacyidea.readthedocs.io/en/latest/modules/api.htmlIssue a simple HTTP request with the credentials
POST /validate/check HTTP/1.1
Accept: application/json
user=username
pass=pin123456
realm=mydomain
Read the JSON response
HTTP/1.1 200 OK
Content-Type: application/json
{
"detail": {
"message": "matching 1 tokens",
"serial": "HOTP0000AB00",
"type": "hotp"
},
"id": 1,
"jsonrpc": "2.0",
"result": {
"status": true,
"value": true
},
"version": "3.1.1"
}Example REST: pam_python
headers = {'user-agent': 'PAM/2.15.0'}
response = requests.post(self.URL + endpoint,
data=data,
headers=headers,
verify=self.sslverify)
json_response = response.json
if callable(json_response):
syslog.syslog(syslog.LOG_DEBUG, "requests > 1.0")
json_response = json_response()
return json_response
305 sloc Python - but it has offline functionality
https://github.com/privacyidea/pam_python/Example REST: simpleSAMLphp
$body = sspmod_privacyidea_Auth_utils::curl($params,
null, $this->serverconfig,
"/validate/samlcheck", "POST");
try {
$result = $body->result;
$detailAttributes = $body->detail;
SimpleSAML_Logger::debug("privacyidea result:" . print_r($result, True));
$status = $result->status;
$value = $result->value->auth;
} catch (Exception $e) {
throw new SimpleSAML_Error_BadRequest("We were not able to read the response from the privacyidea server.");
}
800 sloc PHP - but it has a lot of glue, two modes and enrollment features.
https://github.com/privacyidea/simplesamlphp-module-privacyideaExample REST: Keycloak
JsonObject body = _endpoint.sendRequest(ENDPOINT_VALIDATE_CHECK, params, false, POST);
try {
JsonObject result = body.getJsonObject(JSON_KEY_RESULT);
return result.getBoolean(JSON_KEY_VALUE);
} catch (Exception e) {
_log.error("Verification was not successful: Invalid response from privacyIDEA");
}
646 sloc Java - but it has glue and enrollment features.
https://github.com/privacyidea/keycloak-providerExample stdin: benno mail archive
if not result.get("value"):
syslog.syslog(syslog.LOG_INFO, "Failed authentication")
print("ERROR ERR_AUTH")
sys.exit(0)
else:
# successful authentication
syslog.syslog(syslog.LOG_INFO, "Authentication successful")
user = detail.get("user")
syslog.syslog(syslog.LOG_INFO, "user received")
out = RESPONSE.format(role="USER",
mail=user.get("email"),
displayname=u"{0} {1}".format(user.get("givenname"),
user.get("surname")))
print(out.encode("utf8"))
sys.exit(0)
Endpoints everywhere
/auth- System management, Policies, Events... all configuration
- Token management for users and admins.
- Auditlog and statistics