Two factor authentication or multi factor authentication is ment to raise the bar for attackers. They ought to sniff, brute-force or social-engineer your password and in addition steal or “borrow” your hardware token for a “test”.
Still, I wish to think that the Yubikey – being the product of originally a sole Swedish company – has no back doors. So as long as the TISA does not know of side channel attacks or you used a static password with the Yubikey, you might be fine as long as you get the same Yubikey back – undestroyed.
Nevertheless there are additional measures you can take to improve your security with privacyIDEA.
Disclaimer: This will only help, if you are using your hardware token to authenticate to remote systems. If you use your hardware token to unlock let’s say encrypted harddisk of your notebook, you are carrying, this will not help.
Set up privacyIDEA
When you manage your hardware token for remote access with privacyIDEA and you are crossing borders or you are in situations where you
- think your hardware token could be stolen or otherwise compromised and
- you do not need the token explicitly (since you are on the plane without internet access)
you might want to call your trusted privacyIDEA administrator (some call it help desk) and have your hardware token locked.
This way the hardware token can not be used to access restricted resources. If TISA is still insisting to get your Yubikey, you can say:
“If you take it, you can keep it”
(No of course you can take it back, but you may see it as compromised and you might need to reenroll it.)
If TISA takes the Yubikey there is not use for them, since the token is locked.
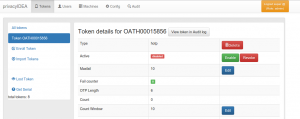
If TISA did not get your Yubikey and you crossed the border, customs or control successfully, you may call your trusted privacyIDEA admin again to reactivate the hardware token.
Conclusion
This might sound a bit complicated but also to simple. But special events like travelling to certain rogue regimes may require special measures.