2FA on-site
Migrating 2FA
to a lasting solution
Texas Linuxfest, 2019 June 1st
Cornelius Kölbel
about me
- Cornelius Kölbel
- 1994 Linux
- 2005 2FA
- Smartcards / Aladdin eToken (eTokenOnLinux)
- HSMs
- 2014 privacyIDEA

contact me
- cornelius.koelbel@netknights.it
- @cornelinux
- @privacyidea

Agenda
- Short Intro to 2FA (as I see it)
- M&A in the security market
- Introduction privacyIDEA
- Migration
- Look ahead
2FA Intro
I am from Kassel, Germany
meet Hercules!
Where are you? Where is your data?
You want secure access - you want 2FA!
What most people think, 2FA is:

What 2nd factors actually are:

Problems
- Users will not stop by at the admin's desk!
- Users are unknown and and spread around the world.
- Users are not tech savvy.
- My device is not supported.
- Which solution and company should I trust?
Things to consider when doing 2FA
- Choose your technology
- Vendor independent
- Backup methods
- Easy to use
- Helpdesk processes
- Workflows
2FA is not only the hand held...

2FA is...
- Infrastructure
- Management
- Workflows
This is why you need
a 2FA management and authentication system
In the past
hardware vendors provided such systems for their (proprietary) hardware
hardware vendors provided such systems for their (proprietary) hardware
Mergers and Acquisitions
Claim:
If your 2FA system looks too good, ...
... it will fail!
Example 1
- ActiveIdentity acquires CoreStreet (PKI)
- HID acquires ActiveIdentity (Smartcards)
- HID acquires CrossMatch (Biometric 2FA)
Example 2
- Aladdin acquires Safeword (from Secure Computing) to get Safeword 2008
- SafeNet acquires Aladdin to get TMS and eToken (TMS → SAM, Safeword 2008 → SAM Express). oups, SAM Express EOL
- SafeNet acquires Cryptocard to get Blackshield (Blackshield → SAS Cloud Service)
- Gemalto acquries SafeNet to what..., oups - SAM(OTP) EOL
- Thales acquires Gemalto to what... HSMs?
Problem with proprietary software and EOL
- You buy user licenses
- End of sales: you can not buy new licenses, even if system is running
- Look out for a new system and migrate!
Migration scenarios
- Migrate to my cloud service
(where you can not migrate away from!) - Migrate to my new onprem service
(which costs up to 10 times of the old software) - Migrate to privacyIDEA!
Introduction to privacyIDEA
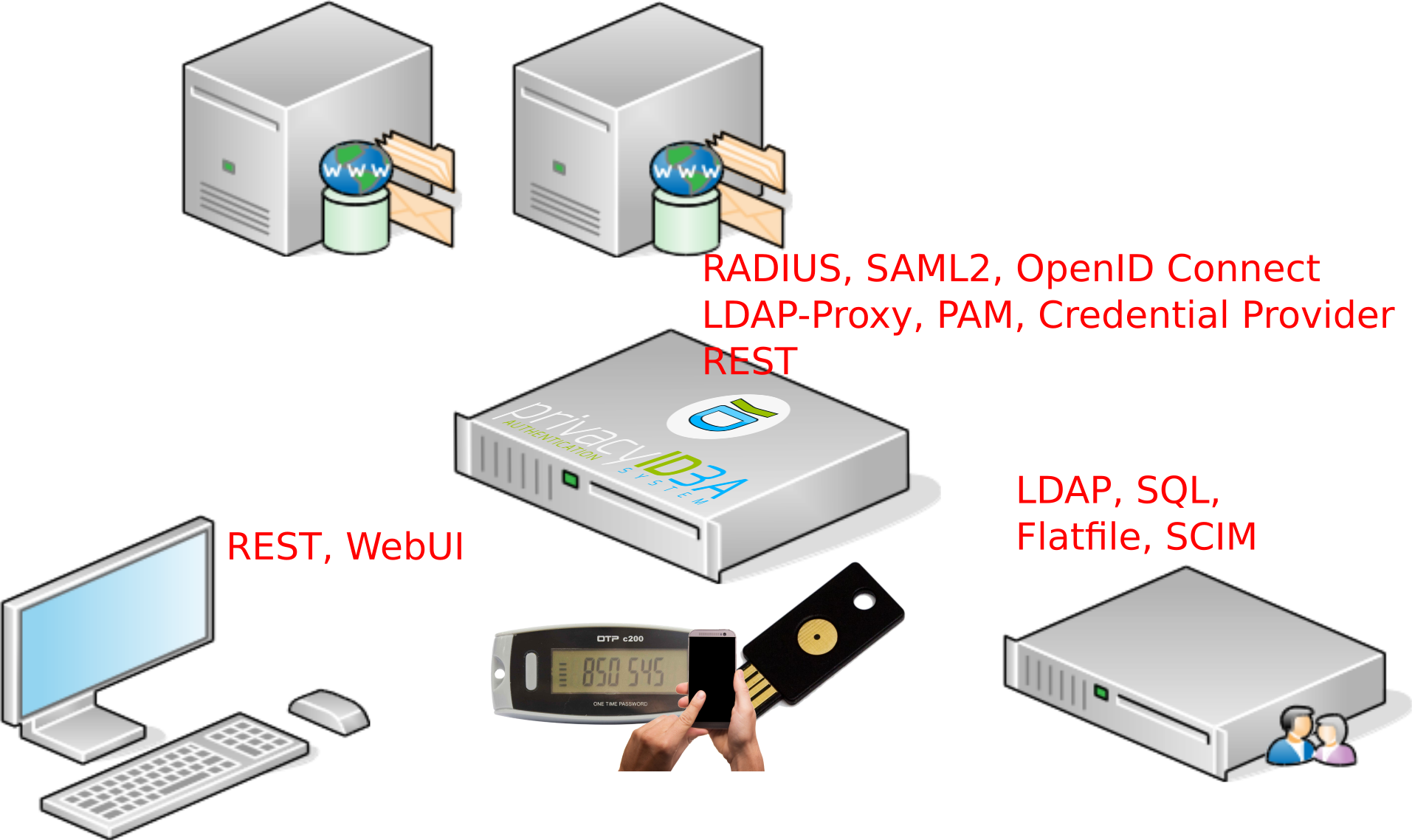
Network structure – where is privacyIDEA located?
History of privacyIDEA
- started in 2005/2006 with the Aladdin eToken NG
- RFC4226 – a standard
- predecessor in 2010
- privacyIDEA fork in 2014
- event handlers in 2016
- won 2 OSS awards in Germany in 2016
Let's check the requirements
Choose your technology
- Supported authentication methods: HOTP/TOTP (including Key Fob and Smartphone Apps), PUSH, Yubikey, U2F, Email, SMS, OCRA, TiQR, SSH pub keys, x509, Paper, Questionnaire, 4-Eyes, Vasco, Registration... (TODO: Smartcards, FIDO2/WebAuthN)
- Written in Python
Token types are inherited from the base class
Some token types are just a matter of a few lines of code. - → easy enhancements without change of:
- ...the installation
- workflows or
- code base. (no need for migration)
- Future proof
From a technology standpoint.
Choose your technology
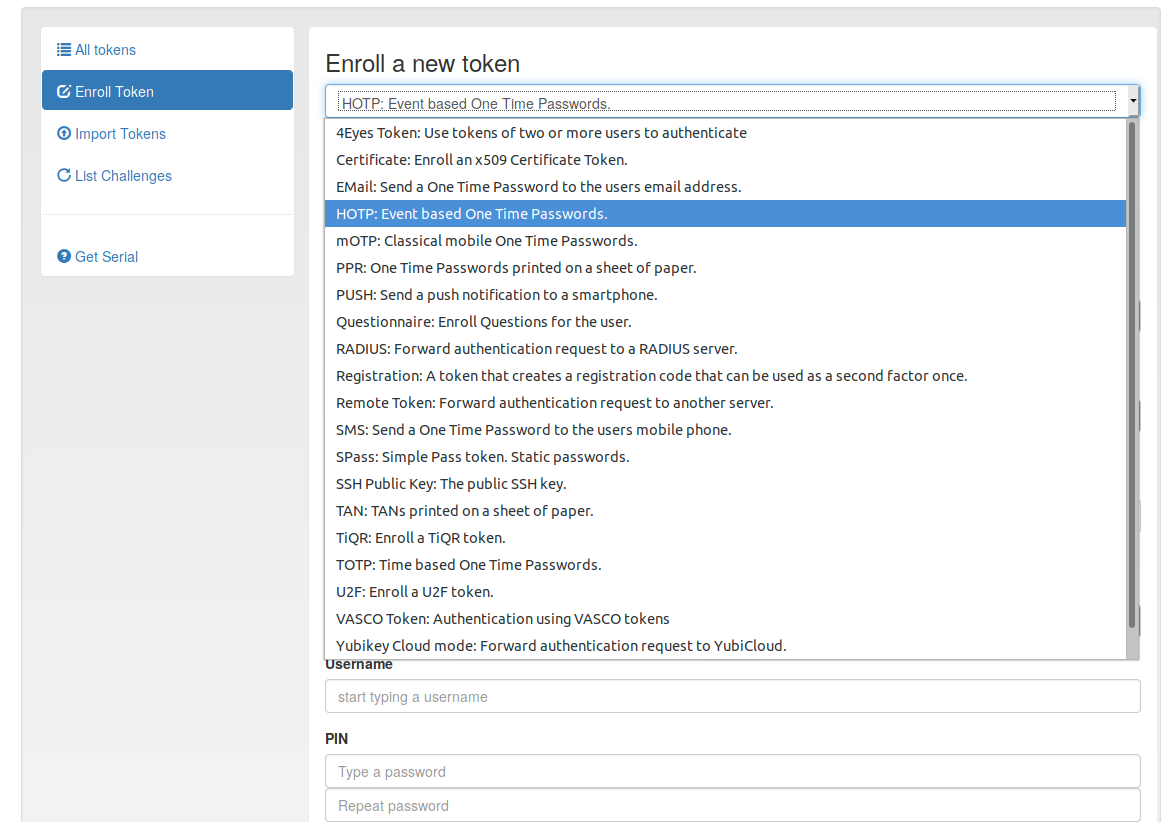
Vendor independent
- Open Source (AGPLv3)
- hosted at Github: https://github.com/privacyidea
- Clone! Star! Fork!
- does not bind to one authentication method of one (hardware) vendor (mix and match!)
- Transparent and independent
- Beware the mergers and akquisitions!
Backup methods
- No personal backup
- One user many tokens.
- Either assign himself, by the helpdesk or automatically.
- Lost Token scenario
Backup methods
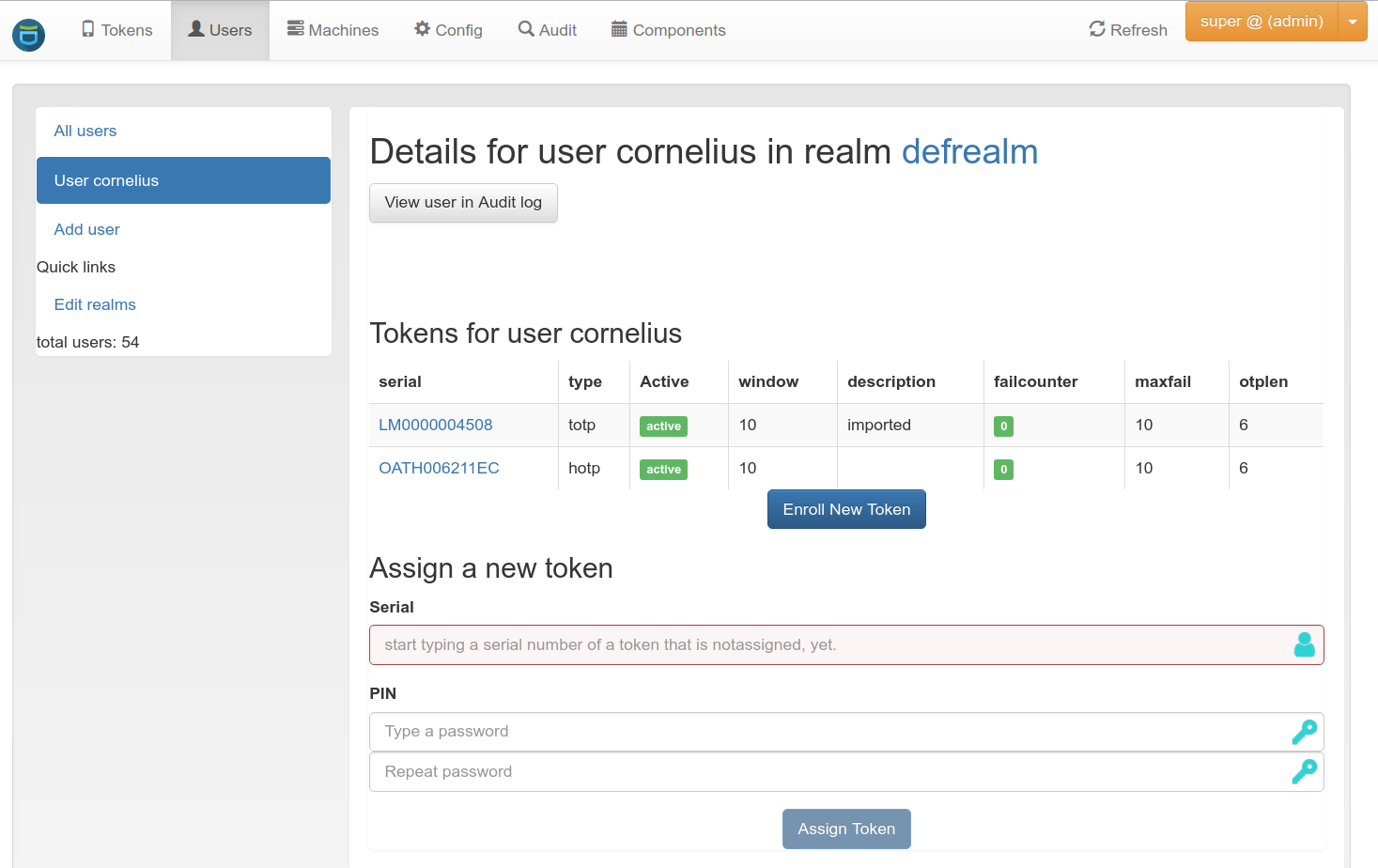
Easy to use
- UI that only allows the configured actions.
- Token wizard.
- REST-API
- → build your own web integration
- Complete API documentation at readthedocs
Helpdesk (processes)
- Policy framework
- define behaviour and response of privacyIDEA.
- Scopes: admin, user, auth, authz, enrollment...
- Work on the API level
- based on users and ldap groups
Workflows
It is all about automation of tedious tasks!- Database level
- Library calls
- REST API
- Event Handler
Workflows - library calls
- Python libs for all tasks.
- No webserver running, no load.
- → external scripts like token-janitor...
Workflows - API calls
POST /validate/check
POST /token/init
GET /token/
DELETE /token/OATH12344
Workflows with Event Handler in privacyIDEA
Fun fact: We developed it, but we do not know what for!What are Event handlers
- Additional actions can be attached to each reqeust
- Pre or Post request
- ...with certain conditions
Event handler classes
- Notification, Token, Federation, Counter, Script
- Each class comes with it's defined actions
send email, send sms, enroll token, set token info, reset failcounter, set counters, run arbitrary scripts, forword to other privacyIDEA machine... -
small code changes => big chances
counter (100 sloc), token (350 sloc)
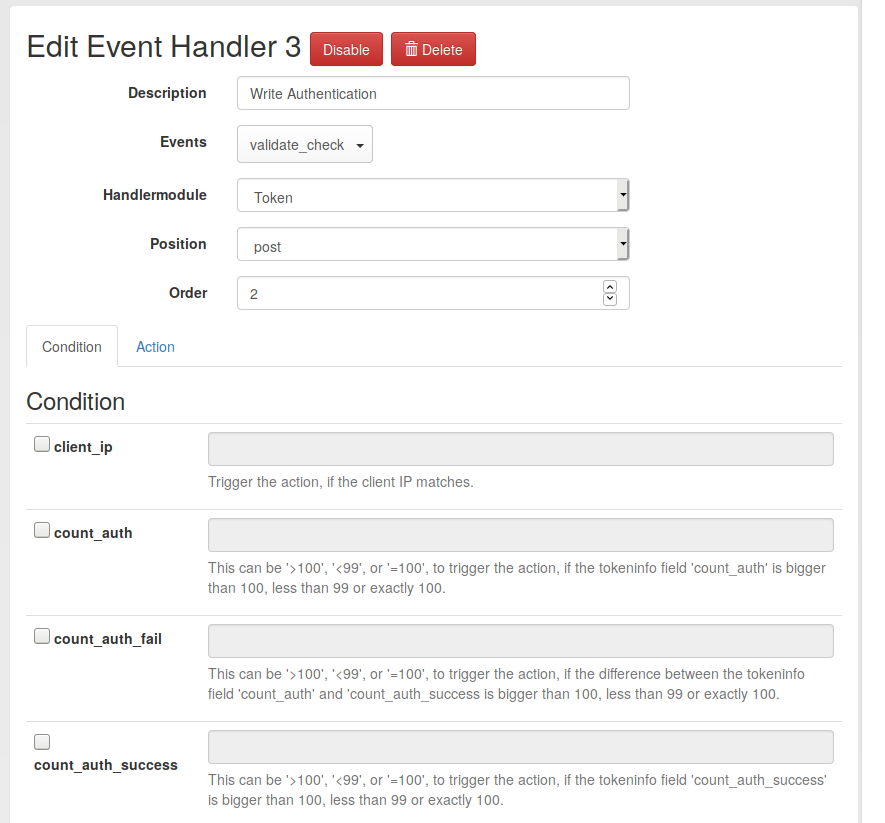
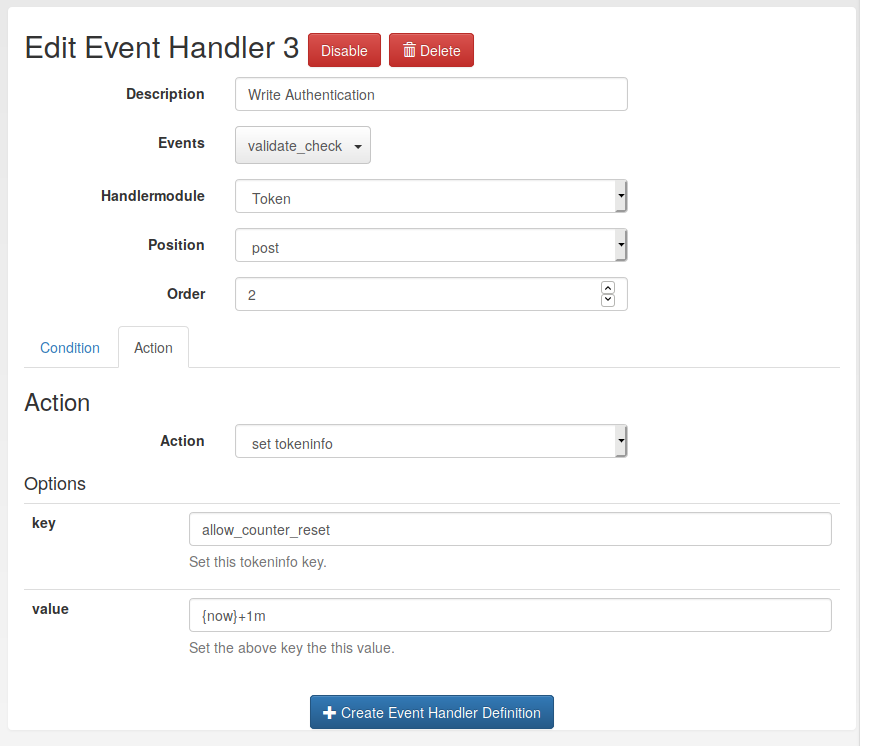
Some handler examples
Notify the user in case of admin action
- handler: Notification
- event: /token/init
- position: post
- condition: user is an admin
- action: send email to token owner
Mark tokens as being enrolled
- handler: TokenHandler
- event: /token/init
- position: post
- condition: user is an admin
- action: set tokeninfo / arbitrary field
- alternative action: disable token
Reset timeshift of a TOTP token in case of successful authentication
- handler: TokenHandler
- event: /validate/check
- position: post
- condition: successful auth
- action: set tokeninfo / timeshift
Count failed authentications
- handler: CounterHandler
- event: /validate/check
- position: post
- condition: failed authentication
- action: increase counter
Print welcome letters
- handler: ScriptHandler
- event: /token/init
- position: post
- condition: administrator / helpdesk user enrolled token
- action: call a script, that prints a welcome letter
Create registration token, if the last token of a user is deleted
- handler: TokenHandler
- event: DEL /token
- position: post
- condition: number of user tokens "0"
- action: enroll registration token
Enroll a token, if the user has none
- handler: TokenHandler
- event: /validate/check
- position: pre
- condition: number of user tokens "0"
- action: enroll email token
Migration
Possible Migration scenarios
- via RADIUS
- via data migration (import seeds)
- via privacyIDEA passthru policy
privacyIDEA talks to RADIUS
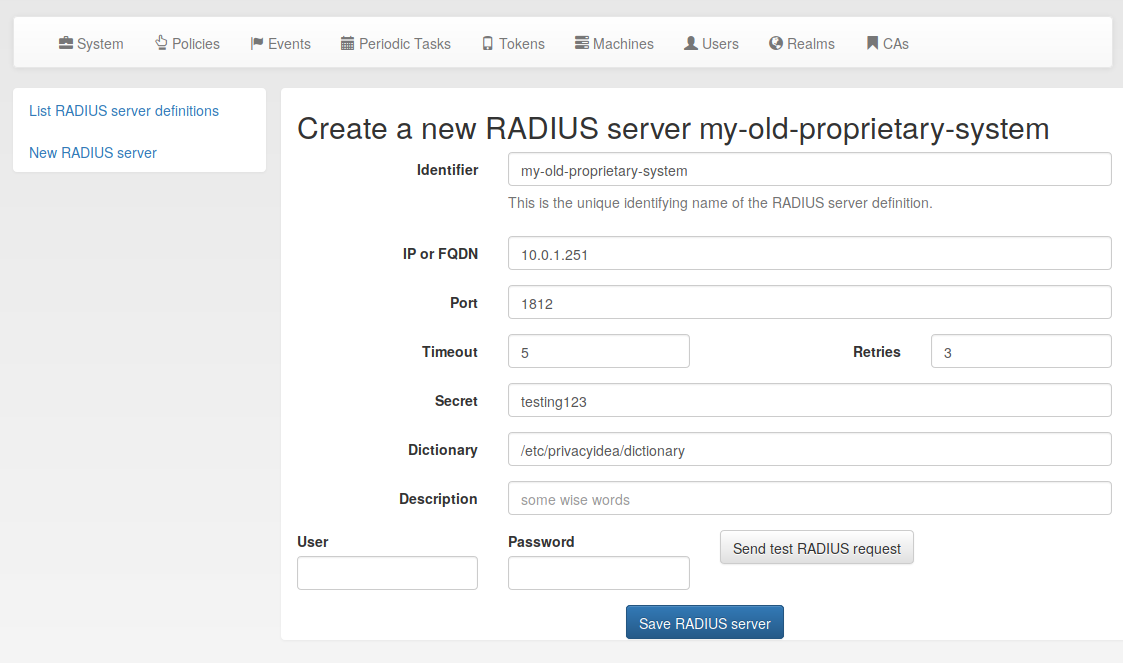
- define (old) RADIUS server
privacyIDEA policy
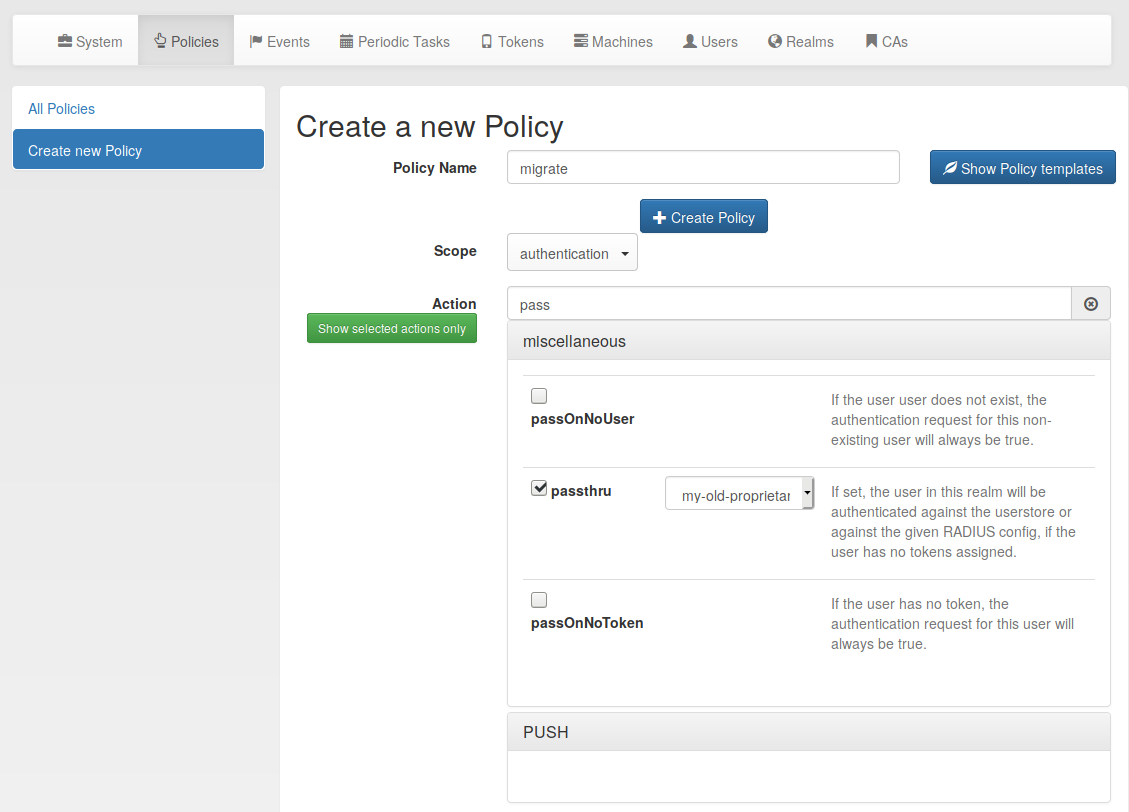
- forward authentication request to old radius
migrating to privacyIDEA
- No need to hurry
- Users can keep their old tokens
- Mix and match
500 old + 10 new - One central audit log
since all auth requests routed in privacyIDEA
Look ahead
Development continues at github
Development continues
- Migrate PIN
- Arbitrary user attributes in policies
- Better support logging to logstash etc.
- WebAuthN
- Central notification system and privacyIDEA news (idea!)
- Smartcard support - start with Yubikey.