A decade of
Open Source
Multi Factor Authentication
SCaLE 21x, Pasadena, 2024-03-16
Cornelius Kölbel
Cornelius Kölbel
- Cornelius Kölbel
- 1973: *
- 1987: J.S. Bach Sonata in A major
- 1988: Got a 80286
- 1992: Study physics
- 1998: Working in IT
- 2004: 2FA (No smartphones!)

Where does Open Source come from?
- 1950s/1960s first Computer hardward was sold to research and universities.
- Software was shippded as "Source Code" as necessary need to run the hardware.
Software Only
- 1970s/1980s Software-Only companies came up. Microsoft (*1975), AT&T Unix System V (1983)
- Software was shipped without hardware.
- "Need" to create revenue with the software.
- No need to ship source code anymore.
Image Credits: elchinator @ pixabay.com
The Open Source!
- 1983: Stallman founded GNU project
- 1985: GPL

Why Open Source?
- Technichians wanted to fix bugs quicker
- Solve problems at lower costs
- Work together
- Scratch your own itch!
See https://en.wikipedia.org/wiki/History_of_free_and_open-source_software
Claim / Problem
There might be problems with no Open Source solution, since there is no personal itch to scratch!?
- ...or the itch is too big, to be scratched by one hand...
- ...or the GNU concept (do one thing, do it right) is misleading...
Scratching your (small) itch in regards to MFA
- rlm_otp works since FreeRADIUS 1 (2004)
only works on FreeRADIUS
- google authenticator libpam
only works on one single machine
- Roughly 150 Wordpress plugins "OTP"
will only work in Wordpress
HOTP - RFC4226
- Before iPhone 1 (2007) hardware vendors controlled the 2FA market.
- Hardware vendors provided closed source software or prorpietary solutions.
- RFC4226 (2004) first allowed hardware vendors to use standardized algorithms.
- Later smartphones to be used as a 2nd factors. 2004
- Still there was no enterprise ready MFA management system (Open Source).
The privacyIDEA project
Open Source multi factor management and authentication system.
est. 2014
privacyIDEA - The ingredients
- Based on a system back in 2010 and thanks to RFC4226
- Started by strong belief in alternatives to and freedom from big players
- Thus chose AGPL
- Bigger itch: Developed by a one-man-show providing consulting and support.
- Chasing a vision: To give a lasting open source MFA solution to the world.
Why "Managment System"?
- Allow to manage thousands of authentication objects under your control. (50.000+)
-
What does Managing mean?
- define and automate processes
- control life cycle of auth objects (token)
- different roles, tasks and access rights
- admins manage all tokens, users manage their tokens
Why "Authentication Systems"?
- Decouple privacyIDEA from application and even from authentication protocol.
- It is no application and no authentication protocol!
-
What does Authentication mean?
- REST API and generic authentication flows
- Plugins for applications (Windows, Linux, nginx, Jitsi, Worpress, Typo3, ownCloud...)
- ...and auth protocols by (Keycloak, Shibboleth, SimpleSAMLphp, Gluu, MS ADFS, FreeRADIUS, PAM)
What is it?
And where?
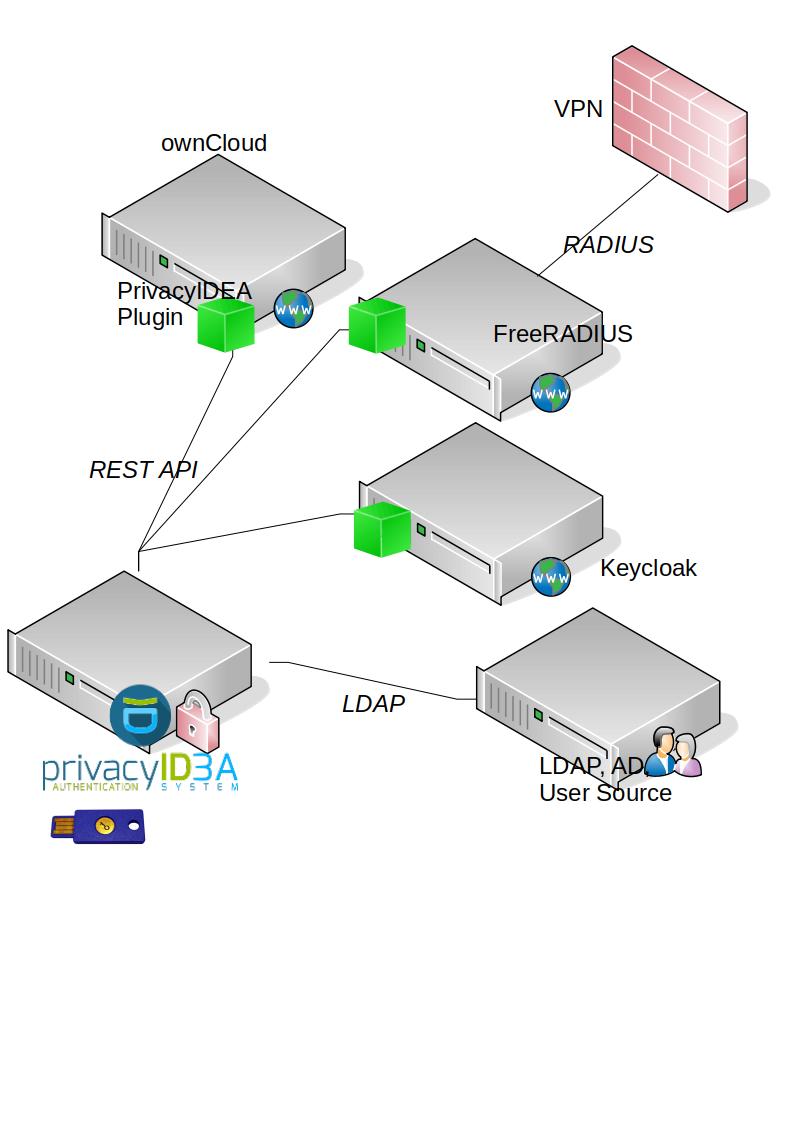
privacyIDEA - Authentication Systems
- Secure Authentication is a matter of smooth workflows.
-
There is not the best 2nd factor!:
- HOTP, TOTP (hardware / apps), WebAuthn, PUSH, Yubikey, SMS, email, remote, RADIUS, 4-eyes, x509, SSH keys, day password, static, questionaire, registration, TAN list, u2f... (see list of token types )
Technical Ovierview
Stack · Deployment · Resolver · Tokens · Policies · Event Handler · Recurring Tasks · PluginsStack
- Single Page Application
- REST API
- Python application (flask)
- Webserver
- SQL Database (SQL Alchemy)
Deployment
- Install via pip, deb, rpm
- redundant database
- node specific configuration (admin node, auth node, selfservice node)
Resolvers and Realms
- Use existing user store (LDAP, AD, SQL, Flat file, SCIM, HTTP)
- Mix and match in realms -> different clients and access rights
Tokens (2nd factors)
- Admins, Helpdesk users, users can assign and manage tokens of users.
- Many different token types
- Multiple tokens per user
- Continuously adding new token types...
Policies
- Behaviour of privacyIDEA
- Scopes: Admin, User, Auth, Authz, Enrollment, WebUI...
- => Role base access
- => Conditions: Different Authentication behaviour in different situations
Event Handlers
- Link additional actions to API call
- Handlers: UserNotification, Token, Script, Counter, Logging, WebHook, CustomUserAttributes, RequestMangler, ResponseMangler
- Conditions
Recurring Tasks
- Event Counter and simple stats
- Currently used to create statistics
- Can run on destinct node
Plugins, plugins, plugins
- Connect applications to the privacyIDEA REST API.
- Community plugins avaiable
- privacyIDEA Team provides:
- ownCloud Plugin, FreeRADIUS
- IdP: Keycloak, SSP, Gluu, ADFS
- Windows and Linux Login
- privacyIDEA Authenticator App, that integrates well with privacyIDEA.
Future and Vision
(We are not developing new algorithms or technologies.)
Technical Vision
- Make admins life easier
- Automate tedious tasks
- Stay open, flexible and transparent: Github: https://github.com/privacyidea/privacyidea/issues
We have destinct ideas:
Ideas at Github- Nested Tokenclasses / Containers
- Pre-Authentication
- Authentication flows (login without usernames)
Philosophical vision
- Offer an Open Source MFA system as defacto standard.
- Continue to be usable in the future without commercial interests.
- Enable others to understand the system and to get in control
How to achieve this?
- Step 1 (done)
Generate money to provide the resources to continously work on the system by founding a company working on and working with the system.
lessons learned: If you find your niche you can also make a living and provide value to the Open Source community at the same time!
How to achieve this?
- Step 2 (Ongoing)
Continuously increase the user base.
Community base is difficult to meassure. (No calling home, different install mechanisms, ~1.4K stars, 993 users in community forum?)
How to achieve this?
- Step 3 (Currently processing)
Go to SCaLE and talk about it!
How to achieve this?
- Step 4 (tbd)
Improve the collaboration on Github
- CONTRIBUTING.md exists
- ~100 contributors. ~10 Paid. less than 8000SLOC of 35000SLOC by community.
How to achieve this?
- Step 5:
privacyIDEA is a distinct human-independable and will never die (vision)
- Let your children go
Your next steps
- Stay in control!
-
Use privacyIDEA!
https://privacyidea.org
-
Talk about it!
https://community.privacyidea.org
-
Contribute!
https://github.com/privacyidea
-
Talk to us!
Come to booth 202!