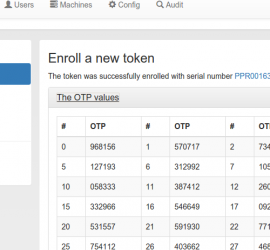
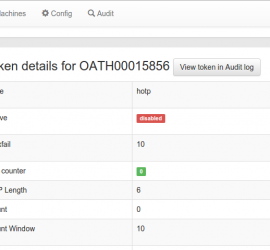
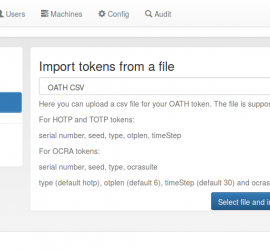
privacyIDEA supports enrollment of PIV smartcards. A from the scratch howto to enroll x509 certificates on Yubikeys.
Yubikey
With SMS OTP a one time password is sent to a mobile phone. The user is supposed to enter this one time password in addition to his static password. This way, the authenticating party thinks to verify, that the user is in the possession of the mobile phone. This is […]
We are proud to announce the availability of privacyIDEA 2.9. Features Yubico Validation Protocol Version 2.9 comes with support for the Yubico Validation Protocol. This way you can use common Yubico client like the PAM module for Mac OS. privacyIDEA’s yubico validation protocol can be reached via /ttype/yubikey. For more […]
Two factor authentication or multi factor authentication is ment to raise the bar for attackers. They ought to sniff, brute-force or social-engineer your password and in addition steal or “borrow” your hardware token for a “test”. Still, I wish to think that the Yubikey – being the product of originally a sole Swedish company […]
This blog will show how you can use privacyIDEA to secure your SSH login. In this case users need to provide an SSH Key and in addition an OTP token and an optional password. Thus you have the following authentication factors: SSH Key (soft possession factor – copyable!) optional passphrase on […]
We just released privacyIDEA admin client 2.5. The admin client already provided an easy way to enroll a bunch of yubikeys by initializing them one after another. Running privacyidea -U https://your.PI.server -a admin token yubikey_mass_enroll you are able to plugin a yubikey, wait for the admin client to initilize it within […]
In Tübingen, Germany will be a new Linuxtag – called Tübix. It is the first time that this event is conducted. The location and the program seems to be very interesting. Cornelius will do a workshop there about installing privacyIDEA, enrolling tokens and authenticating at SSH. You should get an […]
There are some good howtos around, so that you may already have secured your SSH login to your single server using Google Authenticator as described here. Or did you set up a Yubico validation server and configured Yubikey authentication for a bunch of hosts via RADIUS? Today I will show […]