Custom User Attributes and Token Attributes in Policies allow for more control

We are proud to present you privacyIDEA 3.6. Administrators and Users can manage custom user attributes. These additional attributes can overwrite and enrich the existing user attributes, which privacyIDEA reads from the user stores. This way the token administrator in privacyIDEA has additional possibilities to manage the users and to manage the user rights. These user attributes can be used within privacyIDEA policies. In addition policies can now also contain any token attribute like tokentype or fail counter. These attributes and policy conditions help administrators to keep control in larger setups by logically grouping users and tokens.
Policies with Custom User Attributes and Token Attributes
privacyIDEA is no Identity Management. Users are usually managed in an IdM, or only in LDAP or Active Directory. Nevertheless it can be important to add attributes to users – in case the token administrator has no access rights to the IdM or user directory. The administrator can now do so in privacyIDEA 3.6 using custom user attributes. The administrator can even allow users to manage their own attributes. This way the user can e.g. update his mobile number himself, without the need to contact the help desk or the administrator.
Based on these user attributes the administrator can now define policies and thus the access rights can be tuned in more detail.
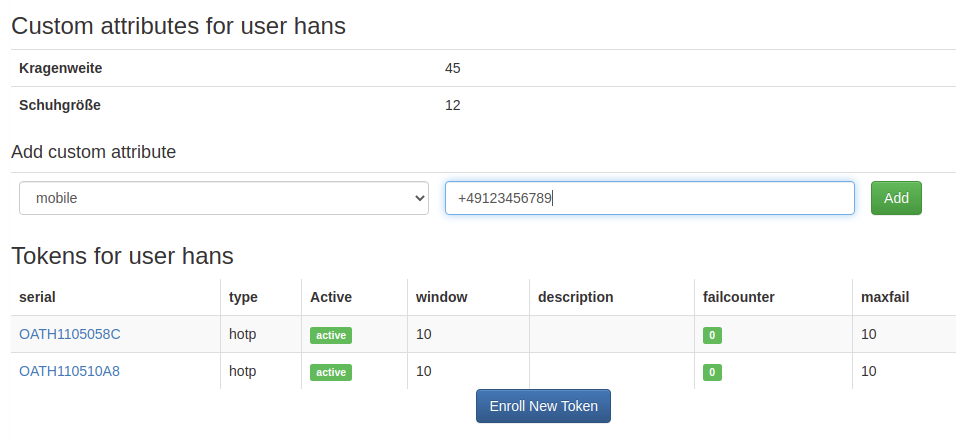
In addition policies can now have conditions on each and every token attribute like description, serial, tokentype, otp length, maximum failcounter, failcounter, active state and more.
This way the administrator could allow helpdesk users to only delete tokens, that have previously been disabled by the user himself. Possibilities are endless.
Simple PUSH Token
Starting with privacyIDEA 3.0 we introduced the PUSH token. If everything works out fine, the PUSH token can work like a charm. But setting it up is quite complicated. Also the Push services by Google and Apple actually do not work that reliably. With privacyIDEA 3.6 the administrator can now configure the PUSH token to only work in a polling method. In this scenario no external 3rd party service is needed and the user’s smartphone only communicates with the privacyIDEA server.
By giving up some comfort such a setup can gain stability and improve the privacy aspect.
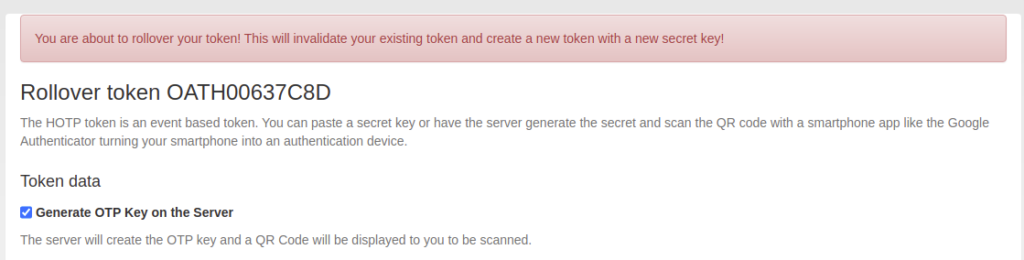
Token Rollover
The administrator can now configure a WebUI policy to allow users to roll over their tokens. This means that the key material is generated anew and the user can enroll the token again, e.g. by scanning a new QR code. This comes in handy, if the user is only allowed to have one token, but wants to move his token to a new smartphone or if the company decides to increase the key size of the tokens.
Enhancements
Besides these main features there are a lot of enhancements. The administrator can use pi-manage to export and import the system configuration. This can be used to move configuration from testing environments to productive environments. You can have different PIN policies for different tokentypes.
In pi.cfg the system administrator can define a custom entry point for the WebUI. This way you can create your complete own WebUI without changing anything in the code.
The token janitor received several improvements. It can export arbitrary user attributes, the seed can either be exported in hex or base32 to increase the interoperability with other MFA systems. The token export can now also contain the user assignment. This way tokens can easily be transferred between different privacyIDEA installations.
You can find the complete Changelog at Github.
Availability
You can download privacyIDEA 3.6 from Github or install it from the Python Package Index. For easy deployment you can use the community repositories for Ubuntu 16.04, 18.04 and 20.04. You can find the installation guidline in the online documentation. If you are updating, it is crucial to read the READ_BEFORE_UPDATE, which contains important information about LDAP resolvers and TLS.
If you want to get involved, be sure to drop by at the community forum. You can also take a look at Weblate, were the community can translate to different languages. We are grateful for the community effort to be able to ship translations in Dutch and French!
For mission critical scenarios the company NetKnights provides an Enterprise Edition with Support.




Note:
Since in 3.6.x, the privacyIDEA server expects url-encoded data, you should also update the privacyidea-radius plugin to v3.4.1 if you use RADIUS clients.